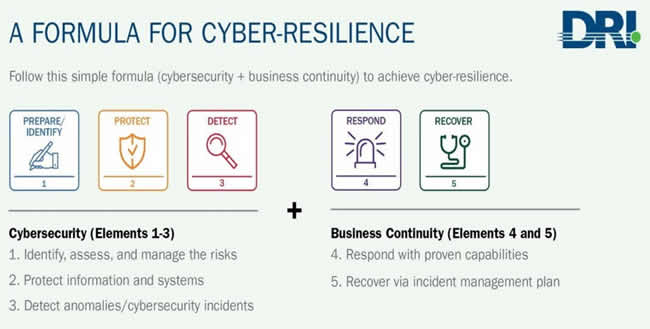
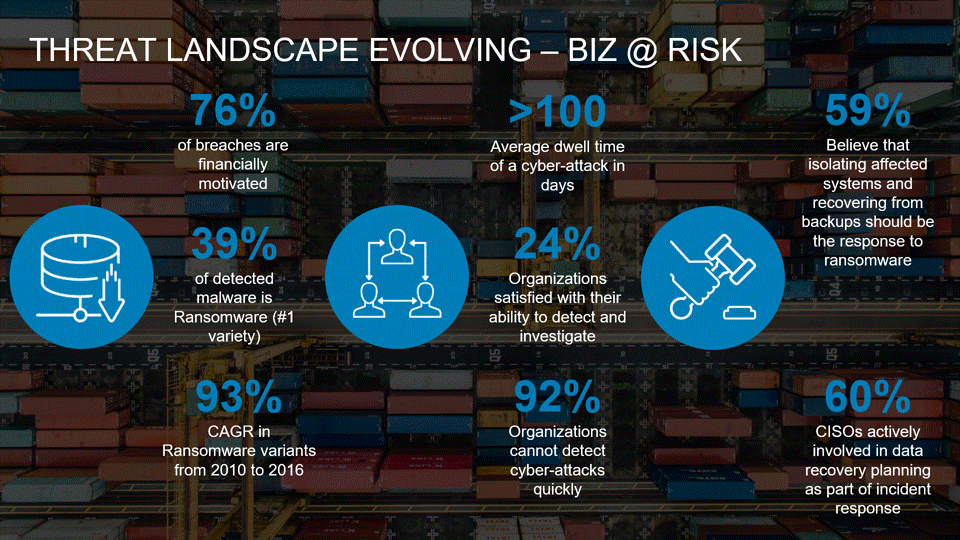
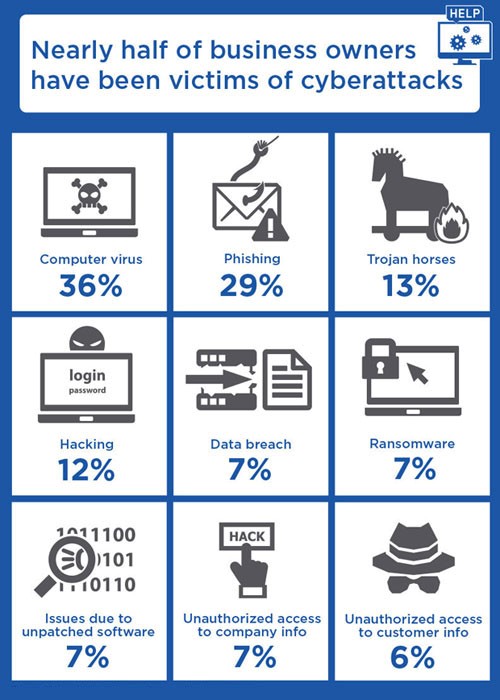
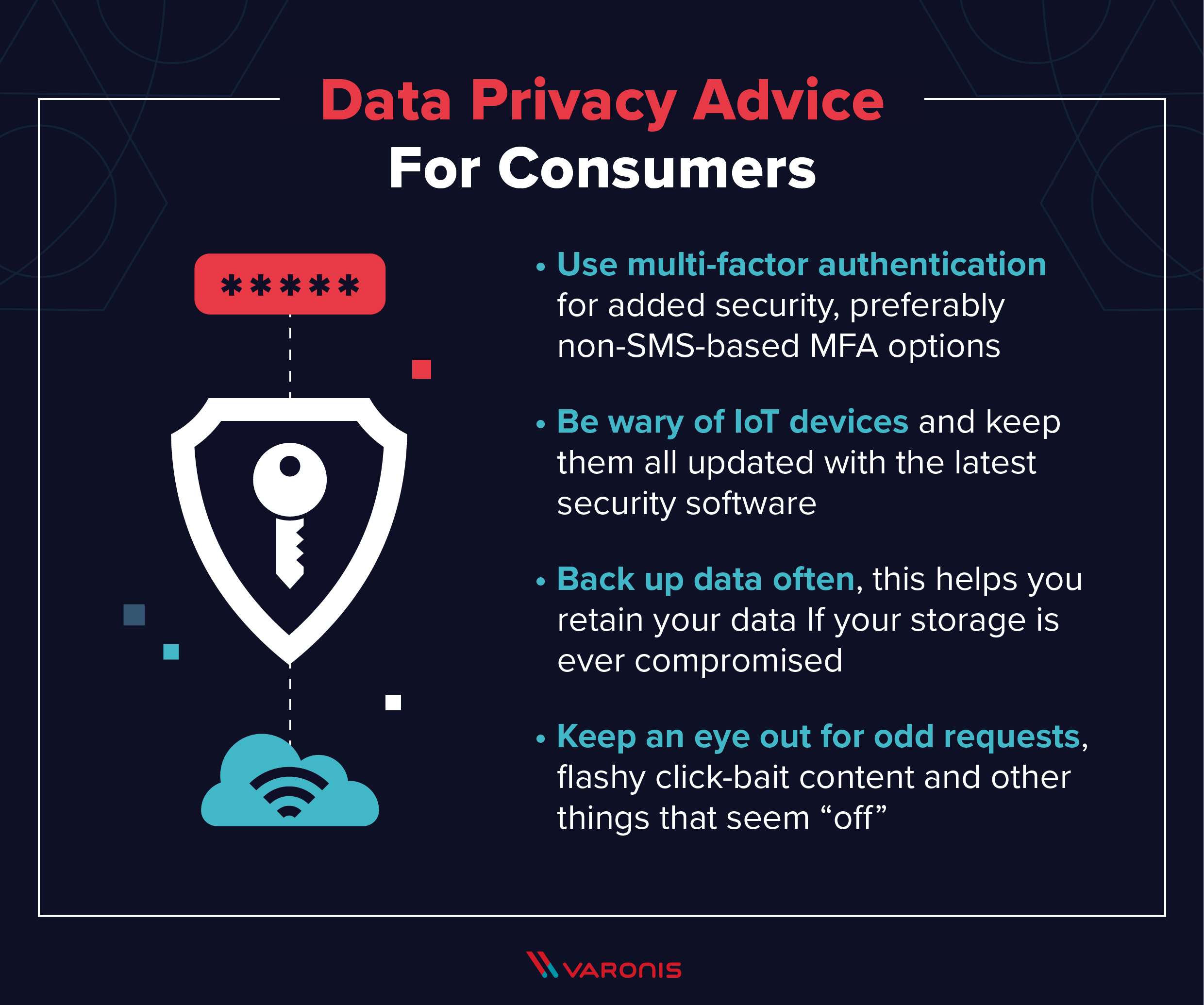
The Single Strategy To Use For Link Fix Tool
Table of ContentsThe Definitive Guide to Link Fix ToolHow Link Fix Tool can Save You Time, Stress, and Money.How Link Fix Tool can Save You Time, Stress, and Money.Link Fix Tool Things To Know Before You Get ThisA Biased View of Link Fix ToolExcitement About Link Fix Tool
It caused me sleepless nights till I found that individuals from Vantage Softech had actually developed this special solution. I installed it, and within a hr I had all links arranged. Just a straightforward yet very smart option. Thanks Vantage.Even more details on the photo insert or connected choices in Workplace, Word files and Expectation e-mails.
Just how can you inform if a picture has been put right into the record or connected? There's no easy means to tell. Right-clicking on a picture gives no clues, not to mention a reference of the link (if any) to an image. There is a way to discover out however it's not straightforward as well as actually buried in Office.
Link Fix Tool - An Overview
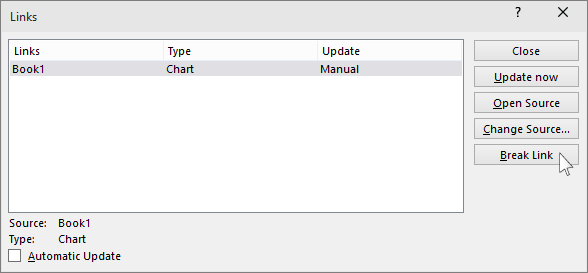
It appears no developers at Microsoft have actually looked at this dialog in many, several years. We'll keep in mind some of the troubles with this dialog box so you don't figure out the hard method. The list of sources does not have the usual column size handles nor is it sortable. That makes it challenging to browse a long listing of links.
Click 'Modification Resource' to pick one more file. That button opens up at the default folder, not the place of the present resource file.: It's tough to see the link in the checklist but select a row and it shows up in the area below the list. Sadly, the link text isn't selectable.
: the type of link, for our objectives it'll constantly be 'Picture'.: is the link updated/refreshed from the resource instantly or just on request (i. e. the Update Currently switch).
The Definitive Guide to Link Fix Tool
Repair the link by replacing the image block with a working picture or photo link. Additionally, most likely to 'Modify Hyperlinks to Files', select the broken link and choose Adjustment Source. Think about making use of the 'Insert and Link' option instead. However, as we've already noted, there's no warning if the link is broken.
The Definitive Guide for Link Fix Tool
If the individual desires to open web links internet in Expectation 2016, the program displays a safety and security notification. The links just no longer job. 7; If the user clicks on a ready web link with an URL, an aggressor can spoof info (e. g. Web, NTLMv2 hashes) from the system.
1 Index 8. 2; If the user clicks on a web link to a particularly crafted URL, an opponent might bypass Microsoft Expectation's protection warning. Even an assault using the preview window in Expectation appears possible if the customer approves a caution. Update KB5002427 (link fix tool) rolled out for MSI setups of Microsoft Office 2016 by means of Windows Update is stated in the blog article Microsoft Workplace Updates (July 11, 2023).
4 Easy Facts About Link Fix Tool Shown
These updates are detailed in the connected CVE web pages. I have actually detailed upgrade KB5002427 for Outlook 2016 below since I got the very first notices regarding it. The problem also influences Click-2-Run setups if they were upgraded to the most up to date construct through Workplace. It's just that I really did not continually her comment is here document these updates below on the blog.
, that reviews translated as adhere to: KB5002427 creates a protection alerting to appear when attempting to open links in Expectation. Relied on locations added by means of GPO in Workplace do not fix it, as well as there's no such alternative under Outlook itself.
Heading: "Protection Advisory for Microsoft Expectation" as well as in the message: "Microsoft Office has identified a prospective safety danger (link fix tool). On Mastodon, Nightfighter, who is additionally suffering from the update, chimed in with the list below comment (translated): Is any individual else having problems opening up links in Outlook considering that the recent Expectation updates?
The Best Guide To Link Fix Tool
Hyperlinks directing to files on network drives( dfs) trigger a mistake message (unforeseen mistake file:/// ) and also nothing takes place. Neighborhood data lead to a security message just like "external" links after uninstalling KB5002427 everything functions.
This morning we have actually begun to see issues to accessing links within emails. Our current configuration is as follows Our sharepoint drives are mapped as a folder structure making use of over here Web, Dav. Manuscript made to run each day check the drives exist and also are still mapped or map the drives if they don't exist to the places of both Job Drive & Personal One, Drive.